### **Chapter 1: Why Cilium – Summary**
#### **Introduction: The Kubernetes Networking Challenge**
Kubernetes has become the standard platform for cloud-native applications. However, its dynamic and ephemeral nature, with workloads constantly scaling up and down, creates significant challenges for traditional networking and security tools. Legacy systems like `iptables` struggle with the scale and churn of microservices.
The rise of **eBPF (extended Berkeley Packet Filter)** in 2014 provided a solution. eBPF allows for running safe, custom programs inside the Linux kernel, enabling deep observability, networking, and security without modifying the kernel. This technology became the foundation for a new generation of infrastructure software, perfectly timed to meet Kubernetes’ needs.
#### **Cilium: Origins and Evolution**
Cilium began in 2015 with a vision to build a new networking layer for Linux containers using eBPF. Its initial, ambitious focus was on IPv6, but it soon added IPv4 support to meet user demands. As Kubernetes became the dominant orchestrator, Cilium solidified around it, rapidly adding features like:
* Multi-cluster connectivity (Cluster Mesh)
* Transparent encryption
* Observability (Hubble)
* Service mesh functionality without sidecars
#### **Industry Adoption & CNCF Graduation**
Cilium’s technical excellence led to widespread adoption:
* **Major Cloud Providers:** It became the default networking layer for Google’s GKE Dataplane V2, Amazon’s EKS Anywhere, and Microsoft’s Azure CNI.
* **CNCF Graduation:** In 2023, Cilium graduated from the Cloud Native Computing Foundation, a significant milestone that signifies project maturity, robust governance, and a sustainable community. It is the **only** Cloud Native Networking project to have achieved this status.
#### **A Flexible and Modular System**
Cilium is not a monolithic tool. It is designed to be **modular** and **fluid**. You can start by using it as a simple Container Network Interface (CNI) and gradually enable advanced features like service mesh, multi-cluster, or encryption as your requirements evolve.
#### **Cilium’s Use Cases**
This chapter outlines the primary use cases where Cilium excels, each explored in detail in later chapters.
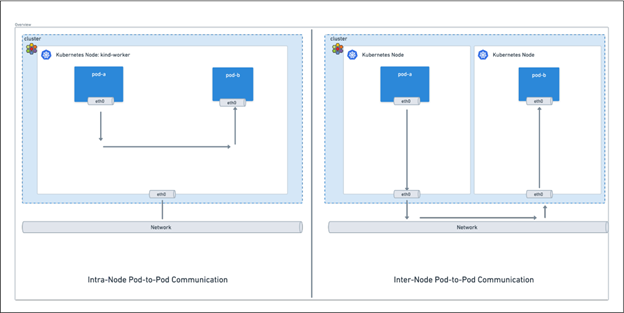
1. **Networking as a CNI:**
* Cilium provides the fundamental network fabric for Kubernetes pods, whether they are on the same node, different nodes, or even in different clusters.
* It handles IP Address Management (IPAM) and uses an eBPF-based datapath for superior performance and scalability compared to traditional CNIs that rely on `iptables`.
2. **Ingress and Gateway API:**
* Cilium implements both the traditional Kubernetes Ingress API and the newer, more expressive **Gateway API** for controlling external traffic entering the cluster.
* It integrates this functionality directly into its eBPF datapath, avoiding the complexity and overhead of additional proxies.

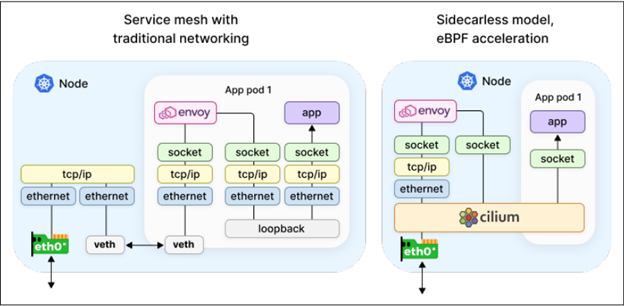
3. **Service Mesh without the Sidecars:**
* Unlike traditional service meshes that inject a sidecar proxy into every pod, Cilium provides service mesh features (like mutual TLS, observability, load balancing) **directly in the datapath** using eBPF.
* This “sidecarless” model reduces resource overhead and operational complexity.
4. **Multi-Cluster Networking and Load Balancing:**
* Cilium Cluster Mesh provides seamless connectivity and service discovery across multiple Kubernetes clusters.
* It also enables advanced load-balancing across clusters, keeping traffic close to the workloads for better performance.

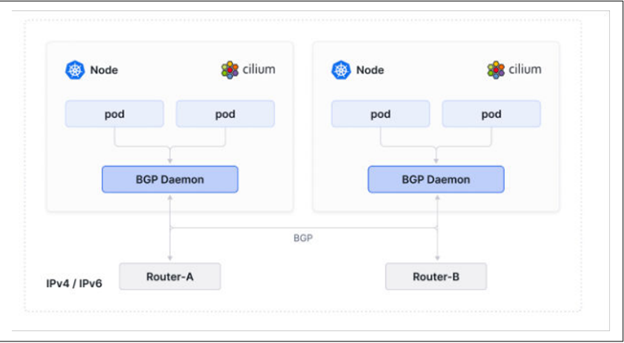
5. **Interconnectivity with the Wider Network:**
* Cilium integrates Kubernetes with the existing enterprise network.
* Its built-in **BGP** support allows it to advertise Kubernetes service IPs to physical network devices (like Top of Rack switches), making cluster services accessible to external workloads.
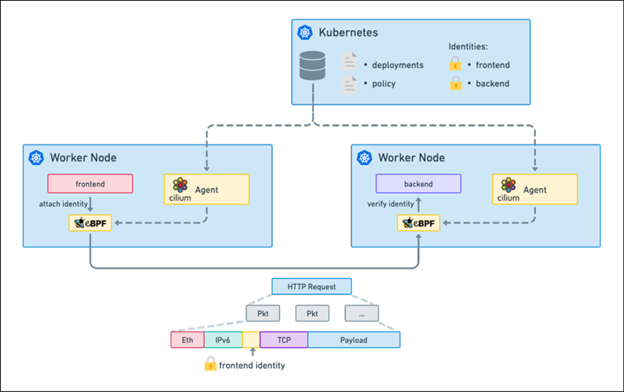
6. **Firewalling and Network Policy:**
* Cilium enforces both standard Kubernetes NetworkPolicies and its own more powerful **CiliumNetworkPolicies**.
* These policies are identity-based (using Kubernetes labels) rather than IP-based, making them ideal for dynamic environments. They can enforce rules at L3/L4 and also at L7 (e.g., based on HTTP paths or API endpoints).
7. **Encryption and Secure Connectivity:**
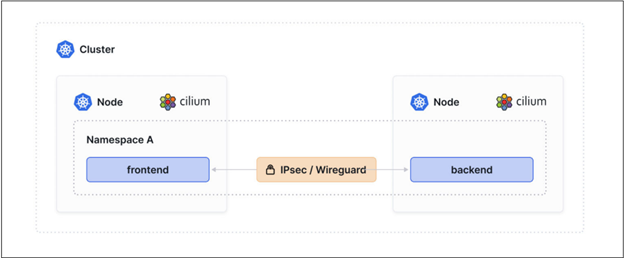
* Cilium provides transparent encryption for pod-to-pod traffic across nodes and clusters using **IPsec** or **WireGuard**.
* It can be enabled with a simple configuration flag, requiring no application changes and handling key management automatically.
8. **Observability with Hubble:**
* **Hubble** is Cilium’s built-in observability platform. Built on eBPF, it provides deep, real-time visibility into network flows, service dependencies, and security policy verdicts.
* It connects application-layer context to network flows, making troubleshooting far more intuitive than with traditional tools.
* Data can be consumed via a CLI or a graphical UI.
#### **Looking Ahead**
The chapter concludes by highlighting Cilium’s ongoing evolution to meet future cloud-native demands:
* Supporting high-performance workloads like AI/ML, which require high throughput and low latency.
* Extending networking and security to Virtual Machines (VMs) managed by Kubernetes via KubeVirt.
* Embracing new Linux kernel features like **netkit** for further performance gains.
* Expanding eBPF and Cilium’s capabilities to other operating systems, like Windows.
As the cloud-native ecosystem grows, Cilium’s open-source, community-driven development ensures it will continue to be a foundational layer for Kubernetes networking, security, and observability.

